This website is made possible by readers. I may earn a small commission when you buy through the links in this article at no extra cost to you. Learn more.
Details
- Price $45 at obdev.at
Overview
For about a few years now, I've become interested in privacy. The idea that your data belongs to you seems simple but is often taken for granted.
At first, I thought that if I had nothing to hide, there was no reason I should care about privacy. As this Reddit comment puts it perfectly, “If you think privacy is unimportant for you because you have nothing to hide, you might as well say free speech is unimportant for you because you have nothing useful to say.” If you have time, you can read this long article on the above argument.
For me, it is a simple concept that what's mine is mine, and it's not to be shared without my explicit permission. That's when I started adopting privacy-respecting options such as using Standard Notes over Evernote, Firefox over Google Chrome. I also started using VPNs like ExpressVPN. I even swapped out Google Analytics to Matome Analytics on this site.
Even with all of the above in play, adopting Little Snitch was the next important step to up my privacy game.
What is Little Snitch and why do you need it?
Simply put, Little Snitch lets you control the connections to and from your computer. Applications and processes on your computer send and receive data. While most of these connections are to make the app work, some of these are for less-desirable reasons, like tracking, trojans, or malware.
While it is always best practice to only install applications you trust, the reality is that even these applications can be compromised due to bad actors or engineering flaws. Safe apps also do transmit data that benefits them at the cost of your privacy, like app dianogstic or tracking data.
Little Snitch gives that control back to you and gives you the reins to control each connection that comes to and from your computer.
What is the difference between Little Snitch and VPN?
A VPN makes you anonymous by first passing your data to a secondary location and then to the destination, making it look like your data, and by proxy, your computer is situated in the secondary location. What's important to distinguish here is the difference between privacy and anonymity.
A VPN does not protect your privacy. Well, not completely at least. A VPN encrypts your data and sends it securely to the VPN's server. This will hide your data from anything in-between, such as your Internet Service Provider or WiFi Portals.
Once it reaches the VPN's server, it is unencrypted and sent to the destination. This means the receiving end can still receive your data and see exactly what it is. Sensitive data like credit cards or private videos can still be exploited.
This used to be an ad.
But no one likes ads, so I got rid of them. If my articles helped you, I ask for your support so I can continue to provide unbiased reviews and recommendations. Every cent donated through Patreon will go into improving the quality of this site.
This is where Little Snitch comes in. It allows you to stop data from leaving your computer to unintended destinations as well as, prevent receiving data from unknown sources.
Usage
How to Use
Understanding how Little Snitch works doesn't take much—you create rules and Little Snitch follows them to deny or allow connections. The anatomy of a rule is also very simple. You allow or deny a process that connects to a hostname. You can set a time limit to the rule or make it permanent.
Since connections happen on your computer all the time, there are two modes that you can do this in—silent mode and alert mode.
Silent mode allows (or denies) all connections till you review the list and manually create rules for them. This might be better for beginners that want to slowly add rules.
Alert mode notifies you of every connection and you have to make a decision on them on the spot. As you can imagine, it will be too much for many to deal with notifications every few minutes. But these notifications will slowly reduce as your rules increase and cover most cases. If you are going to pay for Little Snitch, you might as well put in the effort to make it as effective as possible. This is why I recommend this mode even though it can be a pain in the ass in the beginning.
Little Snitch Rule Group Subscriptions
If you are too lazy to consolidate your blocklists, you'll be happy to know that you can subscribe to user published list, similar to uBlockOrigin. However, compared to some other blockers, Little Snitch rule groups subscriptions are limited and hard to find.
Rule Groups has quite the list of rule groups that you can use, although it's hard to determine which one you actually need.
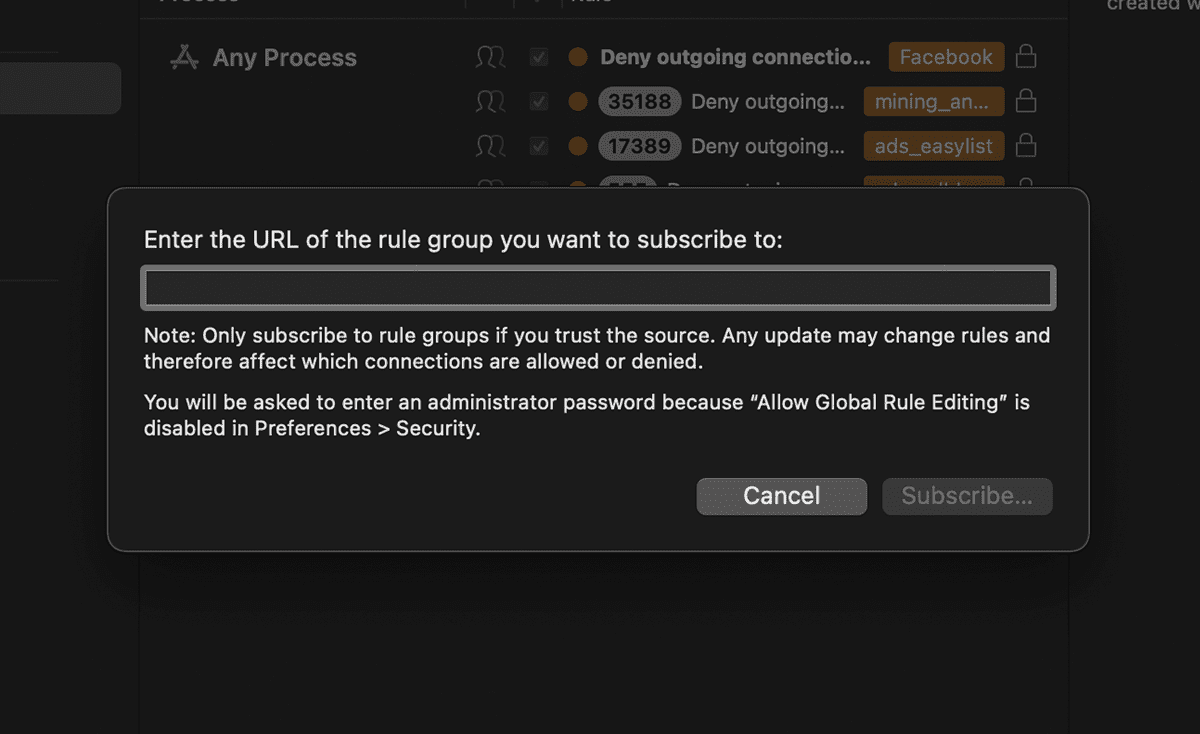
One nice touch is that Little Snitch provides you the ability to manually update the list, in the case the creator is malicious and tries to slip something unrelated in. Although, it would be impossible to manually determine if each URL in the list is safe.
I designed a thing.
I found a 100 year old company that would create these heirloom quality canisters for me. They are handmade and will keep your tea leaves, coffee beans or anything that you need dry for years to come.
or read review
What I would love to see is a Little Snitch curated rule group subscriptions although that seems unlikely to happen.
Another feature that would be nice is the ability to let users create their own Rule Groups, without having to create a list to subscribe to. An example use case is where I want to disable all connections from an application and its helpers until I am using the app.
Rules are easy to set up but hard to decide on
While the setting up of rules is straightforward, knowing which connects to allow or deny is not as straightforward and to me, the most technically challenging part if you ask me.
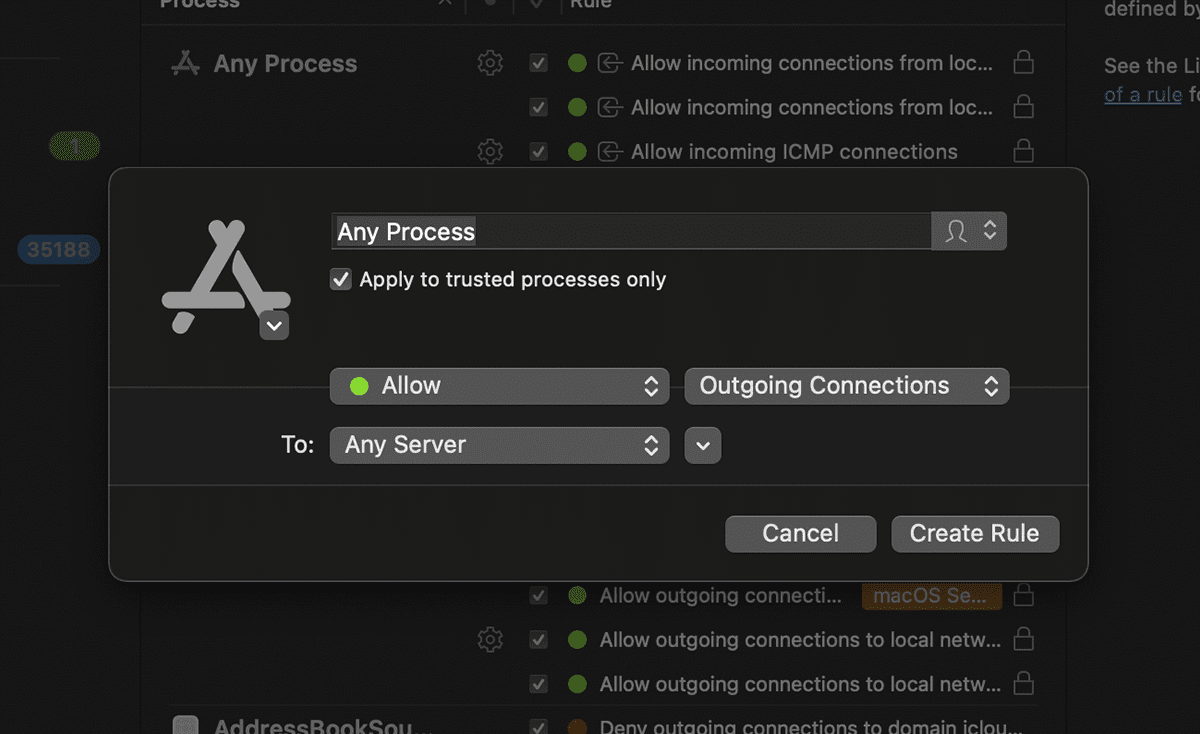
This is because what the connection is for is not straightforward. It will usually come in a form of an IP address or an obfuscated URL. In some cases, hints will be present in the URL.
For example, an alert prompted me if I would like to deny or allow a connection to notify.adobe.io. From the URL, I can tell that this is probably related to Adobe Creative Cloud that I am using and is possible a service to get notifications from Adobe. However, this is all guesswork and there is no way to confirm this. Even searching online will yield uncertain results. If you are mistaken, denying it could result in breaking core functionality, making it an uneasy process overall.
The above can be considered an easy-to-discern example. Most are not the case. For example, Dropbox makes a connection to the 162.125.35.134 which seems to be a Dropbox server upon a web search, but you have no way to determine if this is necessary or not.
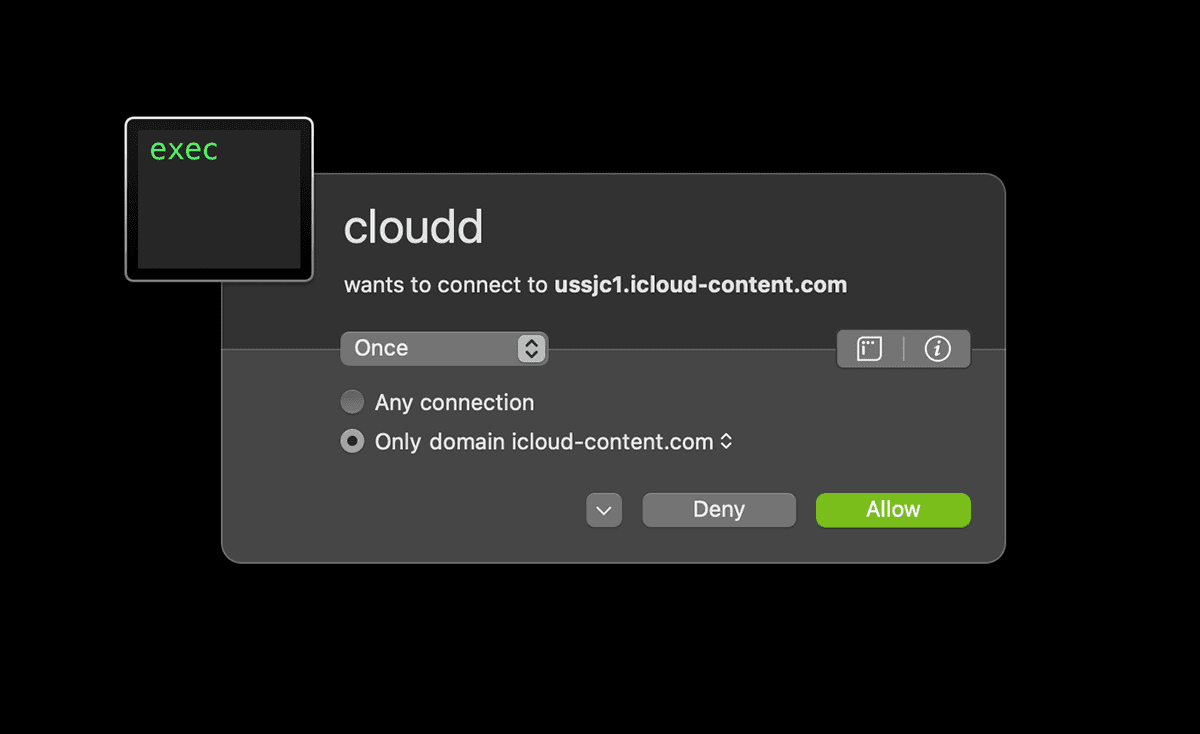
In the below example, I get a connection request to an icloud-content.com hostname. This is a good example of how confusing it can be to judge the necessity connections;
- I cannot tell what this connection is for
- The hostname contains
icloudbut does not useicloud.comwhich means there is a possibility it could be a phishing site - I do not know what the
clouddprocess is
Network Monitor
Little Snitch has actually two applications running, Little Snitch Configuration and Network Monitor. Little Snitch Configuration is where you configure all the rules while Network Monitor actually does the work of filtering connections based on those rules. Therefore, you only need the latter running for the magic to happen.
This is similar to how automation software like Hazel and Keyboard Maestro works.
The Network Monitor shows a summary of connections with the ability to create or change rules of running processes on the fly with just one click.
For example, VLC Player, the video player I use, seems to be transmitting data even when I am not using it. On inspection, it seems to be continuously checking for updates that are not important for me, therefore I swiftly disabled it. For applications like this that have no business making connections, it's safe to simply block any outgoing connections to prevent exposing your furry fetish.
An extreme case is CleanMyMac which has an updater feature that helps update the apps on your computer. To support this feature, they are constantly polling the update server of each application to see if updates are available. This is overkill to me and I disabled it as well.
As you can see, many connections, especially if they are from applications you trust, isn't always malicious. However, Little Snitch offers a whole new level of control to the kind of communication your computer does with the outside world.
Syncing Preferences and Rules
Besides subscribing to a Rule Group Subscription, the only way you can sync rules with other computers is by creating a backup on one and restoring it on the other. This is not very user-friendly and a live sync feature, or at least, allowing users to load preferences from a shared folder would be ideal.
For users of Keyboard Maestro, you'll also find that Little Snitch does not respond to Keyboard Maestro's automation commands. I was trying to automatically load the shared preference file on startup but found that Little Snitch somehow does not accept the commands.
Licenses are OS version specific
When I buy a software, I expect to be able to use it for life. If there are extra features in a new version, I would consider upgrading. However, with Little Snitch, this is not the case.
Their versions are tied to OS versions. So if you buy Little Snitch for Big Sur, and when a new macOS releases, your Little Snitch will no longer work. You would have to buy a new license for the new version that supports the new OS version. While they do offer a discount if you upgraded recently, this is an unfriendly pricing model in my opinion. Since most of us will upgrade our macOS when we can, we are essentially locked into paying for Little Snitch every few years if we want to continue using it.
Most apps that I love like Hazel or Keyboard Maestro will support new OS versions without asking you for upgrades and is what I consider a friendlier pricing model.
Conclusion
Little Snitch, given the need for quite a bit of configuration, is for the intermediate to advanced user. If you're someone who doesn't like to bother with such stuff, might find it too much of a hassle.
For the privacy-enthusiast, Little Snitch does well what no other app does. It is indispensable and a fantastic tool to complement your VPN setup. However, once you get it, be prepared to treat it like a subscription-like cost, since you would have to get a new license each time macOS releases a new version.
Like this review? See all of my in-depth reviews.
Also, consider supporting me by being a Patreon. Every cent given will go back into improving the content of this website.
Tagged little snitch privacy review tech